GCP Virtual Private Cloud (VPC) Networks Fundamentals
VPC networks, sometimes just called as a “networks”. It is a virtual version of the traditional physical network. It provides connectivity for your Compute Engine instances, Container Engine containers and App Engine Flex services etc.,
GCP projects can contain multiple VPC networks. All GCP projects start with a default network and all the GCP resources in a VPC network have an internal IP address that is drawn from it’s subnet.
VPC Networks
VPC Networks Objects
The following are the network objects that you would be dealing with while working on VPC networks.
-
Projects:
A Project organizes all your Google Cloud Platform resources and any GCP resources that you allocate and use must belong to a GCP project. Each GCP project has a project name, project ID and a project number.
-
Networks:
Each VPC network consists of one or more useful IP range partitions called subnetworks or subnets. So VPC networks has no IP address range associated with them. When you create a subnet in a VPC network, you must define a IP address range.
Each subnet is associated with a region. Each network can contain one or more subnets in any given region. VPC networks in GCP is global and it spans all available regions.
There are three types of VPC networks: default network, auto network and custom network.
Each project starts with a default auto mode network. When auto mode network is created, one subnet in each region is automatically created within the network. When a custom mode network is created, no subnets are created automatically and you can have a complete control over custom network’s subnets and IP ranges.
-
Subnetworks
We know that networks have no IP address range. Therefore subnetworks don’t need to fit into an address hierarchy. Subnetworks can be used to group and manage resources i.e., they can represent various departments in an organisation like Marketing, Sales, Development etc.,
Subnetworks can cross zones i.e., subnets can extend across zones in the same region. More than one Virtual Machines (VMs) can be on the same subnetwork but VMs should be in different zone.
A single firewall rule can apply to all the VMs connected to a subnet even though they are in different zones.
-
Regions and Zones
A region is a specific geographical location where you can run your resources. Each region has one or more zones. Resources like VM instances or persistent disks are considered to be zonal resources. And other resources like static external IP addresses are considered to be regional resources.
Regional resources can be used by any GCP resources in that region, regardless of zone. However, zonal resources can only be used by other GCP resources which are in the same zone.
-
IP addresses
There are two types of IP addresses available to Google Cloud Platform (GCP) resources. They are internal IP addresses and external IP addresses. In GCP you can assign IP addresses to certain resources. In particular you can assign an internal and external IP address to Compute Engine virtual machine (VM) instances.
Each VM instance can have one internal IP address which is unique to the VPC network. Internal IP address is allocated from subnet range to VMs by DHCP. DHCP reservation is renewed every 24 hours.
External IP address is reserved from pool (ephemeral). An ephemeral external IP address is an IP address that does not persist beyond the life of the GCP resource. You can also reserve static external IP address , which assigns the IP addresses to your project indefinitely until you explicitly release it.
-
Virtual Machine (VM) Instances
An instance is a Virtual Machine (VM) hosted on Google Cloud infrastructure. You can create an VM instance using Google Cloud Platform Console or using gcloud command-line tool.
A project can have one or more instances. While creating an instance in a project, you need to specify the zone, operating system, machine type etc., of that instance. Compute Engine instances can run the pubic images for Linux and Windows Server.
-
Routes
Routes map network traffic from VM isntance to other destinations. These destinations can be inside your VPC network itself or even outside of your VPC network. Every route has destination and a next hop. In Summary traffic is sent to the next hop for delivery whose destination IP is within the destination range.
-
Firewall Rules
Firewall rules let you to allow or deny traffic to and from Virtual Machine (VM) instances based on your configuration. Though GCP firewall rules are defined at the network level (between your instances and other networks), connections are allowed or denied on individual instance (within same network) basis.
Each firewall rule is defined to apply either for ingress (incoming) traffic or egress (outgoing) traffic. The action taken by the firewall rule is either allow or deny.
-
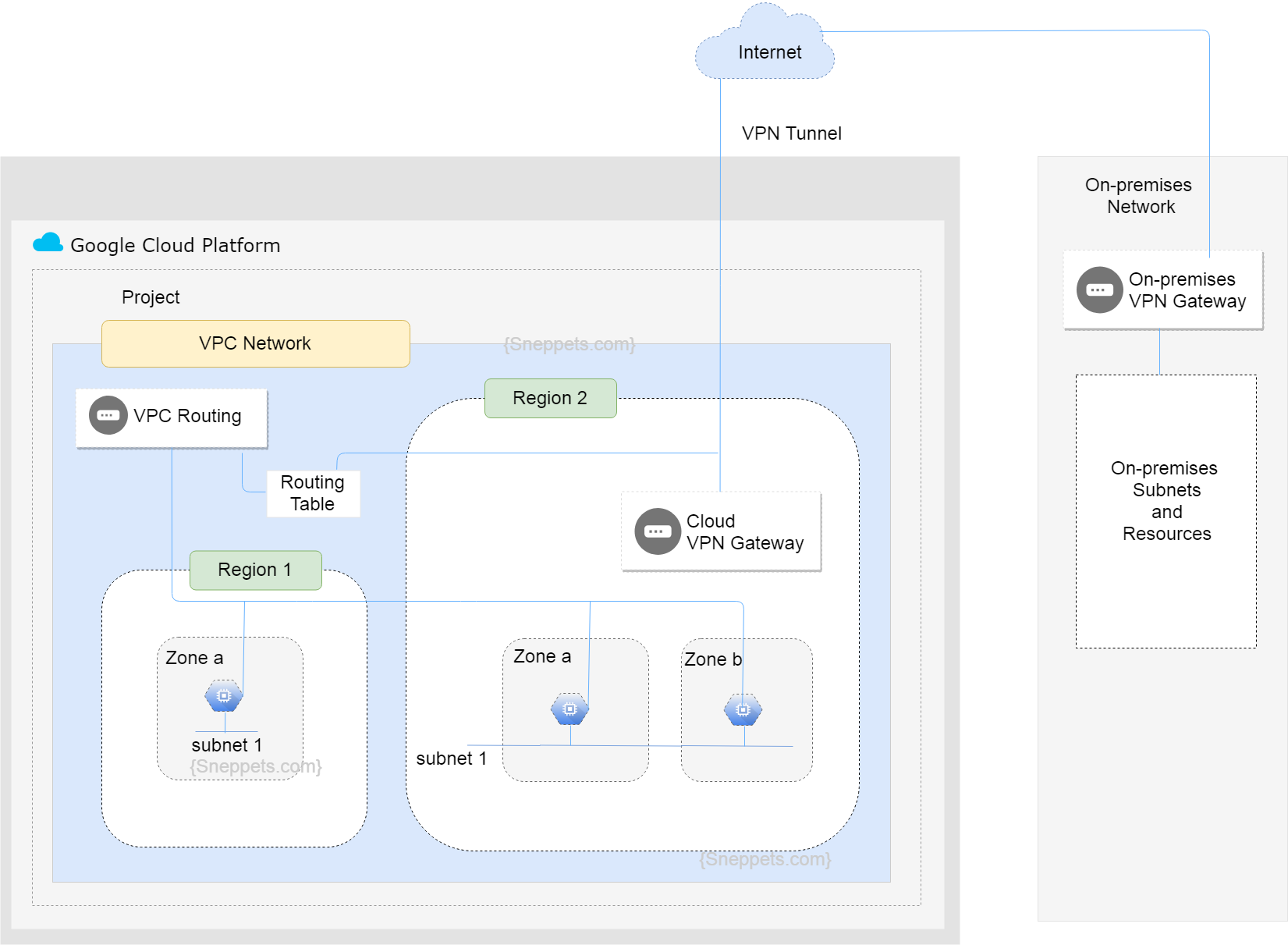
VPN Gateways
A virtual Cloud VPN gateway which runs in GCP is managed by Google using the configuration specified by you in the project. Each Cloud VPN gateway is a regional resource using a GCP regional external IP address. A cloud VPN gateway can connect to an on-premises VPN gateway or another Cloud VPN gateway.
-
VPN Tunnels
A VPN tunnel is used to connect two VPN gateways and it is the medium through which encrypted traffic is passed. Therefore to create connection between two VPN gateways, a pair of VPN tunnels must be established.